Table of contents
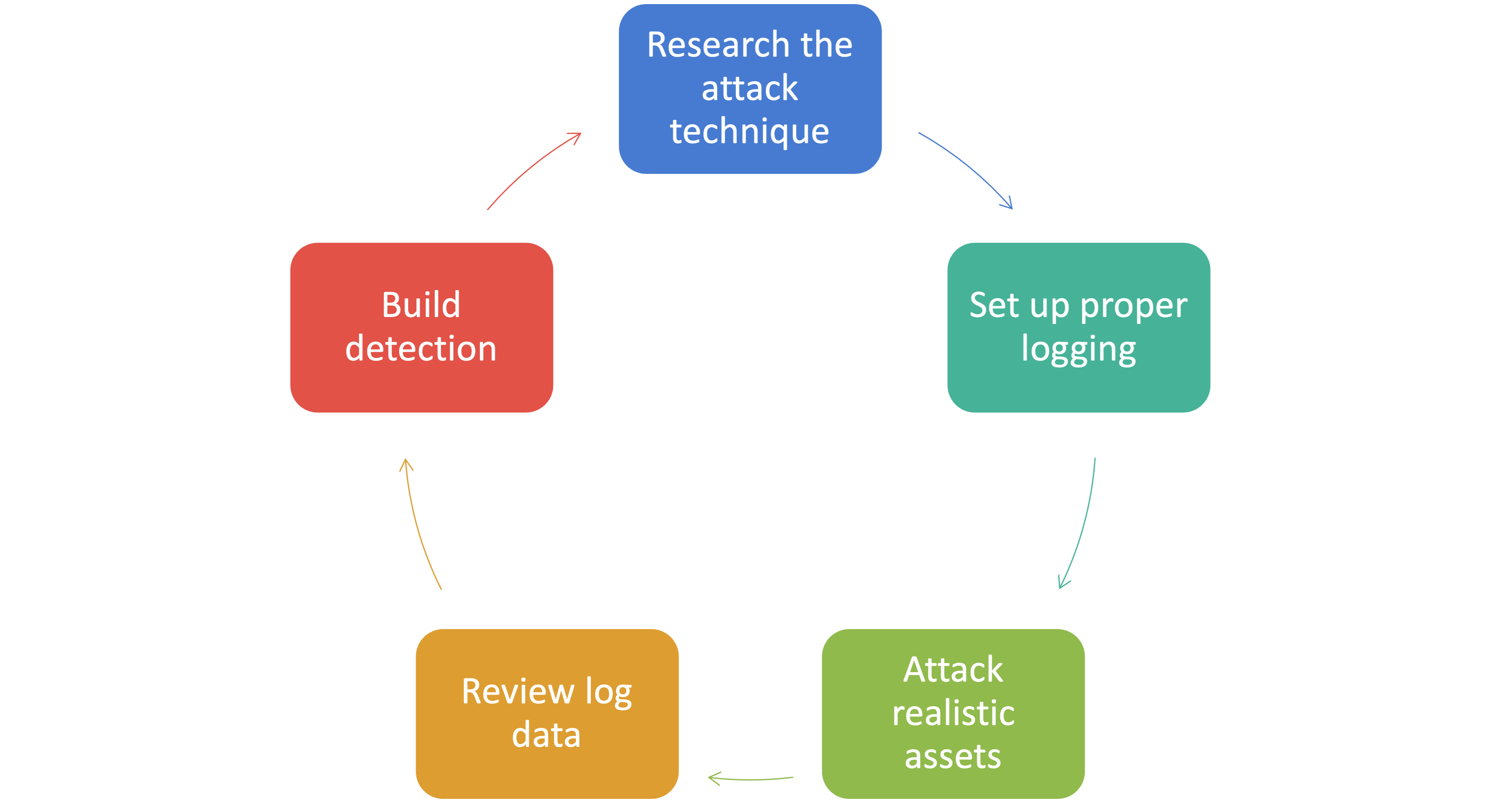
Lifecycle Process
Research the attack technique — Lab 1
Set up proper logging — Lab 2
Attack realistic assets — Lab 3
Review log data — Lab 4
Build detection — Lab 5
Prerequisites: An AWS account with administrator access
NOTE: In this lab, you will be attacking your AWS Account. So please do not use your AWS Production Account.
Disclaimer
This lab write-up credits SANS for the Workshop on Building Detections in AWS. It replicates the workshop guide by the Cloud Security SANS Team. Following the instructions may result in an AWS billing of around $2, considering prompt resource deletion after completing the lab.
Lab Objective
The overall process and takeaways will be:
Establish proper logging to detect adversarial activity
Perform the attack to generate the appropriate artifacts
Review the log event data
Create an automated process to quickly discover this activity
Test that the automated process is working effectively by “re-attacking” the AWS account
This exercise aims to enhance your skills in detecting and responding to potential security breaches, as well as improving your understanding of AWS security features.
Lab Exercise
Reference
Website walkthrough: https://building-detections-aws.sanscloudwars.com/
Video Walkthrough: https://www.youtube.com/watch?v=FZKZuNk49Dw
