Lab Objective
You will act as an attacker in the following ways to generate log data, which will help build your detection and automation:
Perform discovery of S3 resources - ATT&CK Technique T1619 (Cloud Storage Object Discovery)
Download an interesting file - ATT&CK Technique T1530 (Data from Cloud Storage)
Challenge 1: Perform ATT&CK Technique T1619 (Cloud Storage Object Discovery)
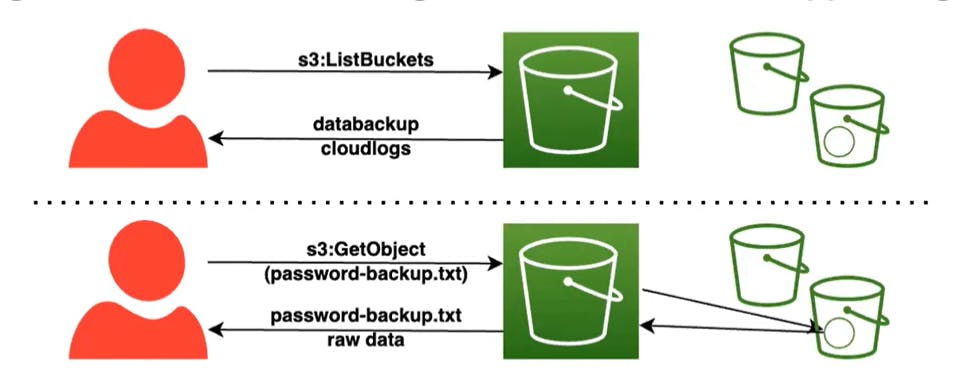
Using either the AWS Management Console or the AWS CLI to perform reconnaissance (discovery) of the S3 buckets in the AWS Account. You will find out that one file contains some interesting data that an attacker may be tempted to download.
Assuming the Attacker is using the AWS Management Console.
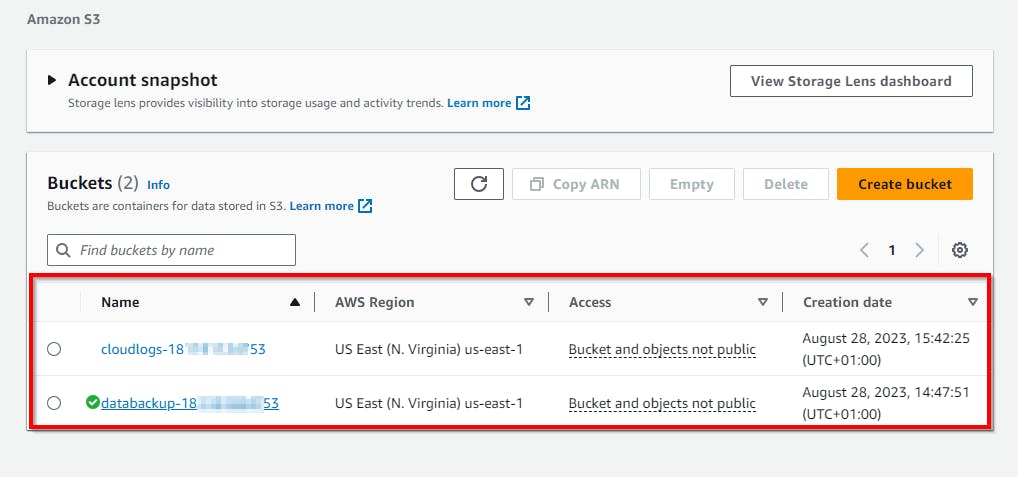
- He/she will navigate to the storage service (Amazon S3) console, and among the S3 buckets, the bucket name
databackup - 18119*****53looks interesting to view.
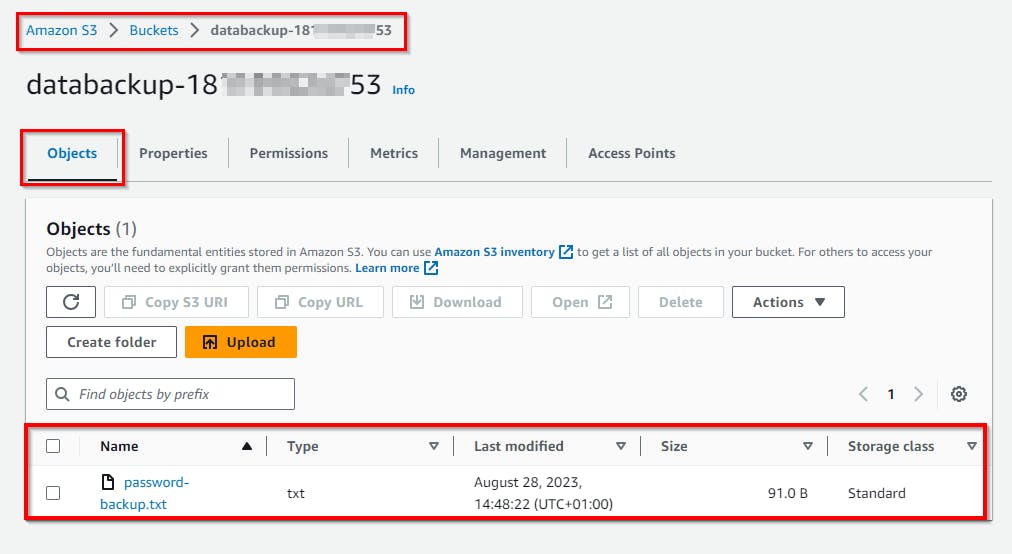
- On clicking on the Bucket name
databackup - 18********53, the object within the bucketpassword-backup.txtlooks enticing because it might contain secret passphrases to accounts that the attacker can use for malicious purposes.
Assuming the Attacker is using AWS CLI to perform reconnaissance
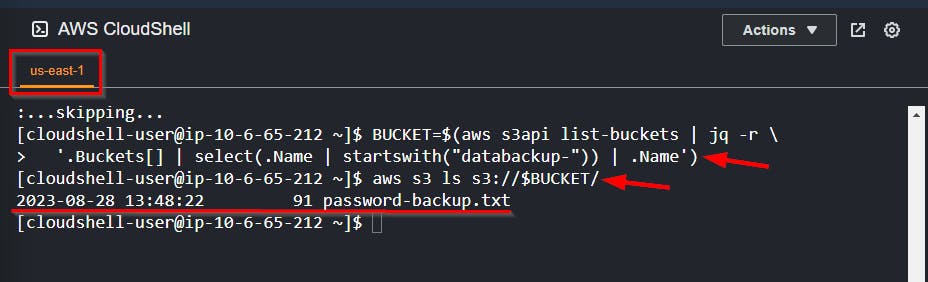
- Navigate to AWS CloudShell and run the command to view the list of S3 buckets in the AWS Account.
aws s3api list-buckets

press
qto exit.
- From the listed buckets
cloudlogs-$AcctNumanddatabackup-$AcctNum. To check the contents within the buckets fordatabackup-$AcctNumwhich looks interesting to view, run the command.
BUCKET=$(aws s3api list-buckets | jq -r \
'.Buckets[] | select(.Name | startswith("databackup-")) | .Name')
aws s3 ls s3://$BUCKET/
To view the content (object) for cloudlogs-$AcctNum , replace databackup- with cloudlogs- In the above code
Challenge 2: Perform ATT&CK Technique T1530 (Data from Cloud Storage)
Having discovered compelling content within the databackup-$AcctNum bucket, the attacker will attempt to download the files. This mirrors the attack approach used by the threat group Fox Kitten to exfiltrate files from targeted cloud storage instances.
The attacker might download the files either via the AWS management console or AWS CLI
Assuming the Attacker is using AWS CLI
The attacker can use aws s3 cp or aws s3 sync operations to download data from the S3 bucket.
- Use the
cpcommand to copy the txt file to the home directory
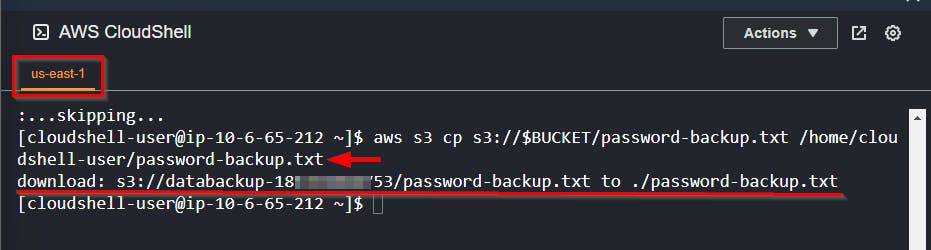
# Command to Copy file to home directory
aws s3 cp s3://$BUCKET/password-backup.txt /home/cloudshell-user/password-backup.txt
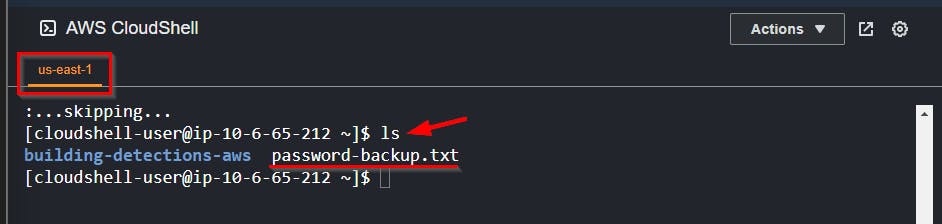
- Use the command
lsto list content in the current working directory.
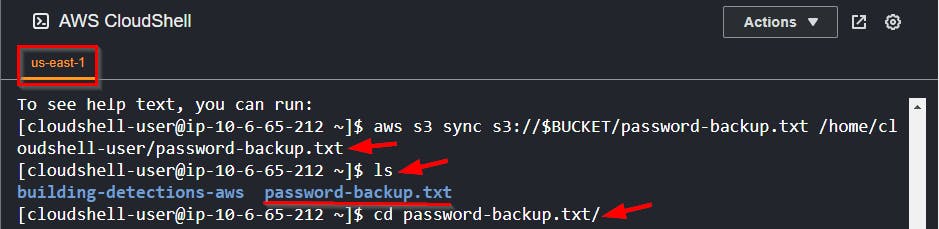
- Use the
synccommand to download the Txt file to the home directory.
#Command to download file to home directory
aws s3 sync s3://$BUCKET/password-backup.txt /home/cloudshell-user/password-backup.txt
Great job! You've successfully simulated an attacker's actions of discovering a file they're interested in, downloading it, and then examining its contents.
Having successfully located and retrieved the honey file, the upcoming exercise will delve into methods for recognizing this access.
