MITRE ATT&CK Technique T1530: Data from Cloud Storage
Attackers can exploit the misconfiguration of cloud storage solutions on AWS, such as Amazon S3. Despite security guides provided by providers, misconfigurations remain common. This vulnerability has led to incidents of public access to sensitive data due to unintentional misconfigurations, posing the risk of exposing critical information like credit cards and personal records. Attackers might also leverage leaked credentials from source repositories or logs to gain unauthorized access to cloud storage objects.
Lab Scenario
You will be playing an attacker's role in accessing a honeypot file
A honey file is a deceptive resource created to attract and monitor unauthorized access attempts within an AWS environment.
You are a member of the AWS security team responsible for monitoring and securing the company's cloud infrastructure. You have received intelligence that suggests a potential attacker may attempt to access sensitive information within your AWS environment. To proactively identify and mitigate this threat, you will create a honeypot file and set up monitoring mechanisms to detect any unauthorized access attempts.
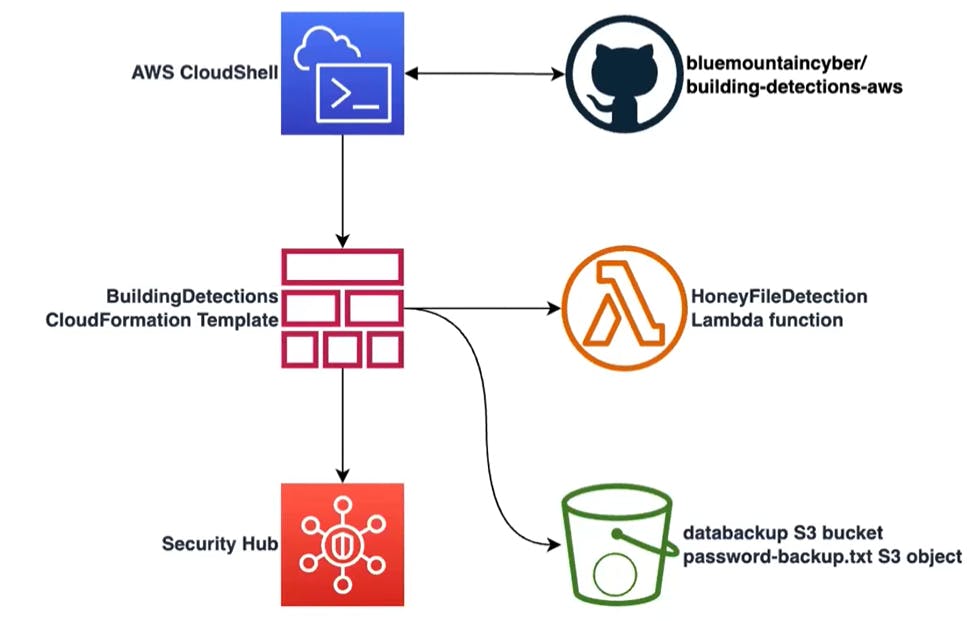
In this exercise, you will use AWS CloudShell to clone a GitHub repository containing a CloudFormation Template. This template will facilitate the deployment of Infrastructure as Code (IAC) components, including a Lambda function, an S3 bucket, and Security Hub configurations.
Lab Objective
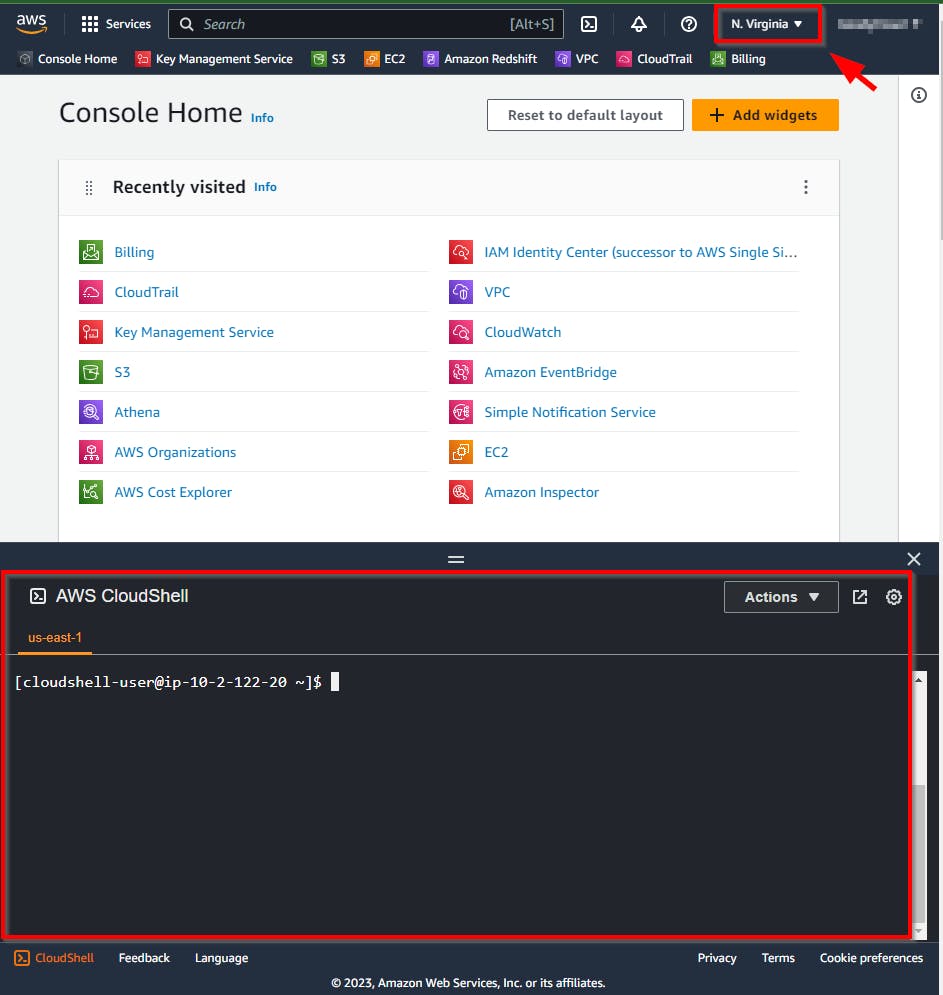
Log into your AWS account and launch a CloudShell session in the N. Virginia (us-east-1) region.
Download the source code using
gitfrom the workshop GitHub repository.Deploy workshop resources using AWS CloudFormation and verify resources were successfully created.
Lab Task
Challenge 1: Account Setup
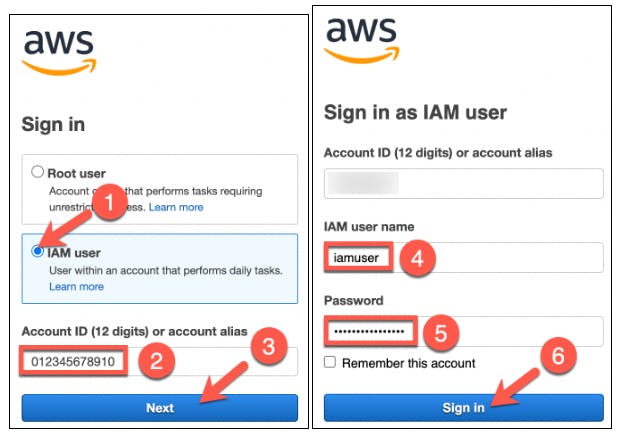
- Log into your AWS Management Console as an IAM User with Administrator Access (Pls ensure you are not using Prod Account)
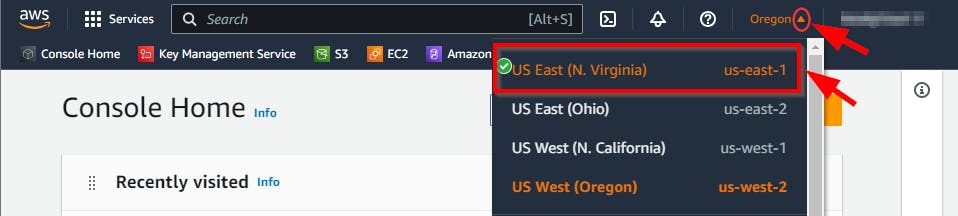
- On your AWS Management Console, change your region to N. Virginia (us-east-1)
- Now, launch CloudShell by clicking the Icon close to the search box or at the footer of your screen. (NB: The cloudshell pops up at the bottom of your screen)
NB: CloudShell session expires after roughly 20 minutes of inactivity.
Challenge 2: Deploy Infrastructure from GitHub
To help you quickly prepare realistic targets for this lab and set up time-consuming resources that aid automated detection, clone the repo provided which also includes Infrastructure as Code (IaC) in the GitHub repository.
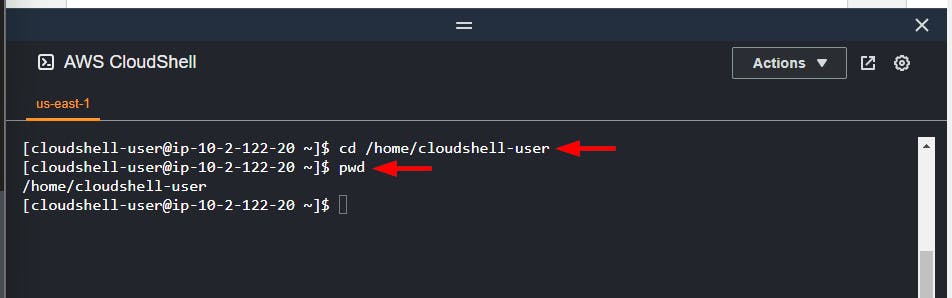
NB: Ensure you change the working directory to the home directory using the command:
cd /home/cloudshell-user
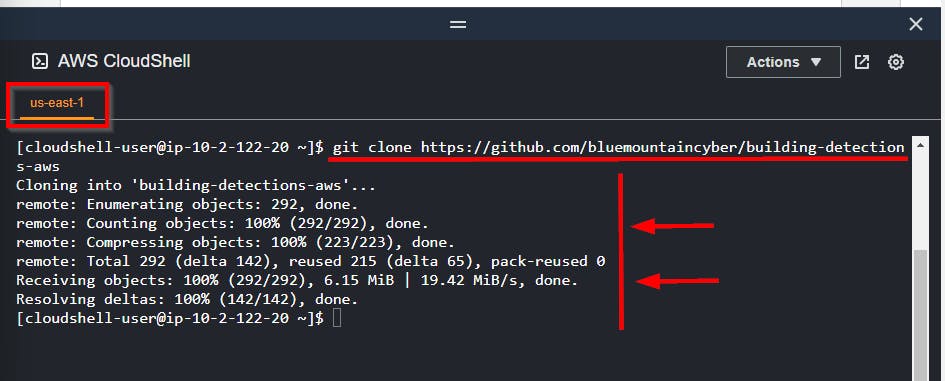
⇒ Now clone the Github Repo using the git command:
git clone https://github.com/bluemountaincyber/building-detections-aws
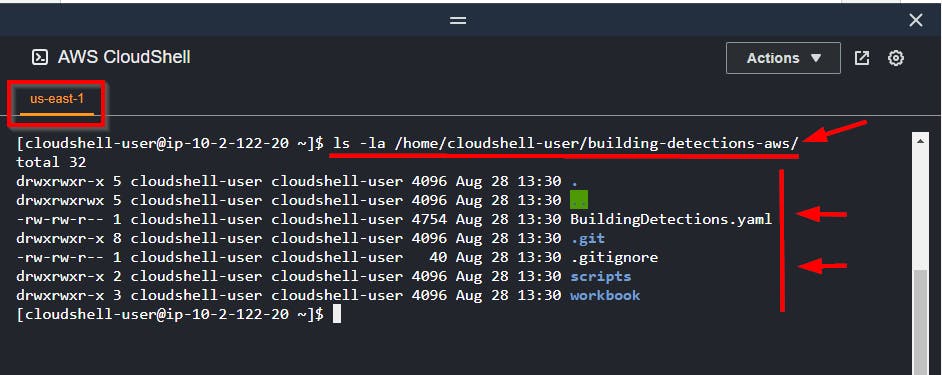
⇒ Run the command to confirm that the GitHub Repo was successfully cloned (downloaded)
ls -la /home/cloudshell-user/building-detections-aws/
Challenge 3: Deploy IaC Resources
Finally, you have all of the components needed from the cloned Github repo to deploy resources such as the Lambda function, an S3 bucket, and Security Hub configurations in your AWS account.
NB: If you already have Security Hub setup in your AWS account within the N. Virginia region (us-east-1), your deployment will fail. The Error looks like this
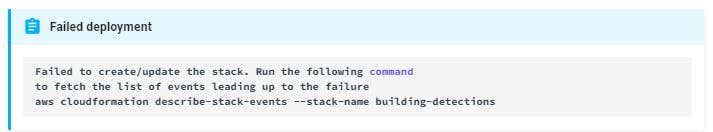
If that happens, you can run the following commands after this failure and try again:
# If that happens, you can run the following commands after this failure and try again:
aws cloudformation delete-stack --stack-name building-detections
aws securityhub disable-security-hub
Note: Use
build.shto deploy the IaC (which can be found in thescriptsdirectory of the repo you just downloaded). Ensure that all works properly by searching for the following AWS resources using the AWS CLI (also provided in CloudShell):
Resources to be deployed:
⇒ A honey file named password-backup.txt
⇒ An S3 bucket with a name beginning with databackup- with a honey file placed inside called password-backup.txt
⇒ Lambda function named HoneyFileDetection
⇒ Security Hub is successfully deployed
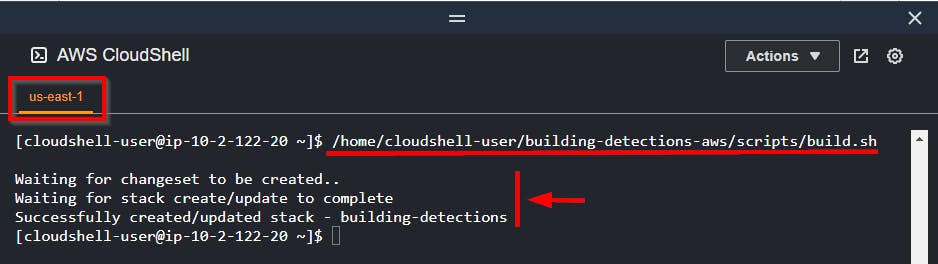
- Run the
build.shscript located in the/home/cloudshell-user/building-detections-aws/scriptsdirectory. After roughly 2 minutes, it should be complete.
/home/cloudshell-user/building-detections-aws/scripts/build.sh
Next, Confirm if the Resources were successfully deployed
Run the command to get the S3 bucket details with the name
databackup-and its contentsBUCKET=$(aws s3api list-buckets | jq -r '.Buckets[] | select(.Name | startswith("databackup-")) | .Name') aws s3 ls | grep $BUCKET aws s3 ls s3://$BUCKET/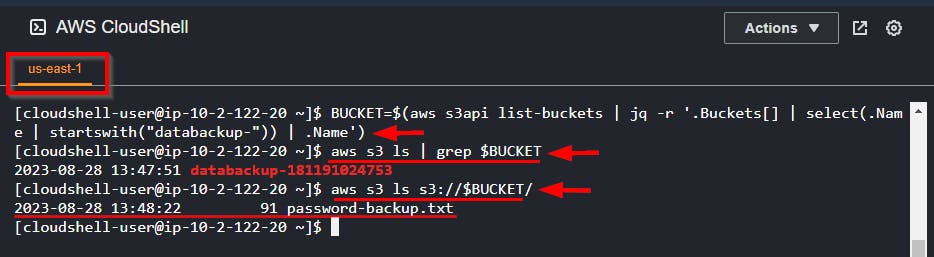
Run the command to get the Lambda function named
HoneyFileDetectionaws lambda get-function --function-name HoneyFileDetection --query Configuration.FunctionArn --output text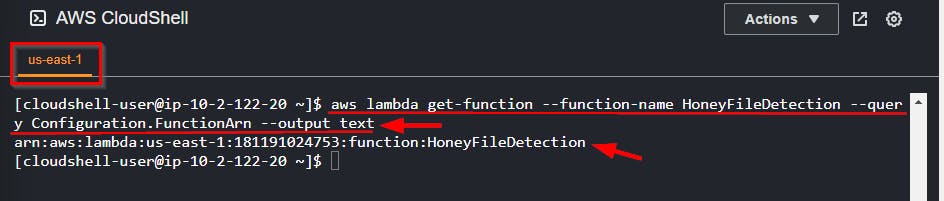
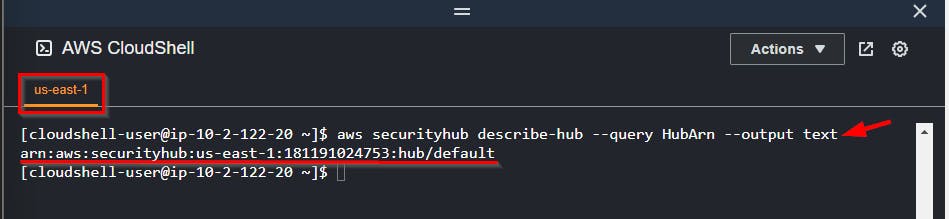
Run the command to check the Security Hub deployment status
aws securityhub describe-hub --query HubArn --output text