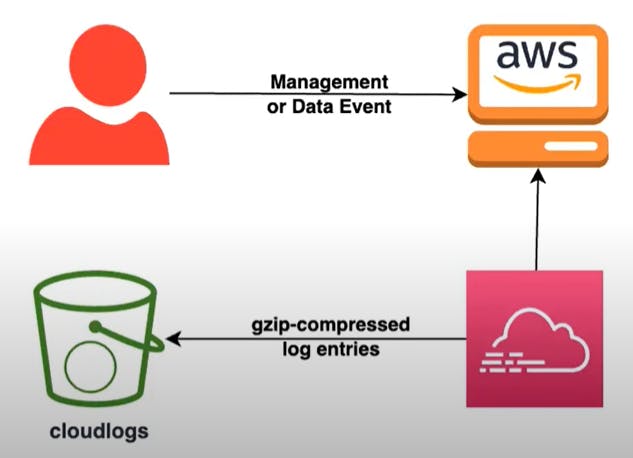
Cloud Visibility through Cloud Management Event Logging and S3 Object Access Logging would help achieve comprehensive visibility into the cloud environment.
Cloud Management Event Logging involves capturing and analyzing events generated by various cloud services, enabling a granular understanding of user actions and system behavior. Amazon S3 (Simple Storage Service) Object Access Logging, on the other hand, focuses specifically on the storage and access of objects within S3 buckets. It provides detailed records of who accessed objects, when the access occurred, and the type of access (read or write).
Lab Objective
Research ATT&CK Technique T1078.004 detections and discover an approach to use in your AWS account.
Create a log collection in an S3 bucket
Enable CloudTrail trail capturing management and data events
Lab Task
Challenge 1:Read through ATT&CK Technique T1078.004
- Navigate to the MITRE ATT&CK Technique T1078.004 page and read through.
Summary: Attackers can gain access to cloud accounts and misuse the credentials for activities like initial access, persistence, privilege escalation, or evading detection. Cloud accounts, created and managed by organizations, are used for users, remote support, services, or administration. These accounts might be linked with traditional identity systems like Active Directory. Compromised credentials can lead to data theft and network access. Attackers could also move laterally if they compromise federated cloud accounts. Once access is gained, attackers might manipulate accounts, adding roles to maintain control and increase privileges.
In the Procedure Examples, you will see the known threat groups that have used this technique and how it was used to their advantage. A popular threat group LAPSUS$ (G1004) recently used compromised credentials to access cloud assets within a target organization, Uber.
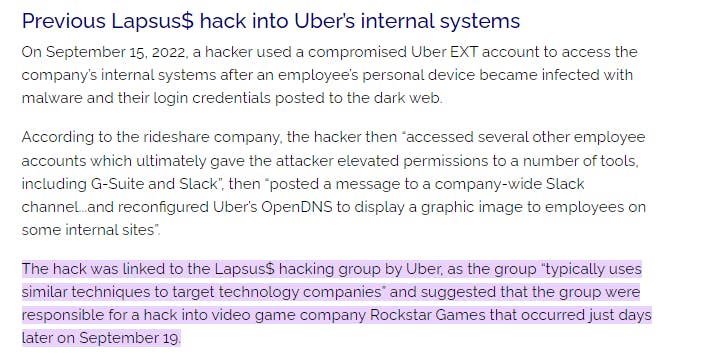
Source: Cyber Security Hub
The Mitigations section shows how we, as defenders, can limit the attacker's chances of using this technique
Finally, the Detection section shows some techniques to discover this behavior in a cloud environment.
Honey files are essentially decoys strategically placed within our organization's critical areas. If someone tries to access them, we quickly notice and react because it signals that an unauthorized person is attempting to breach our systems. But here's the question: How exactly do we keep an eye on these honey files and spot when someone's trying to get to them?
Challenge 2: Create Log Collection S3 Bucket
To monitor the access to a honey file effectively, it's necessary to track its usage. This involves setting up a CloudTrail Trail within AWS, enabling S3 data events. However, before setting this up, you need to establish a designated storage location. This data will be stored in a separate S3 bucket, serving as the repository for this information.
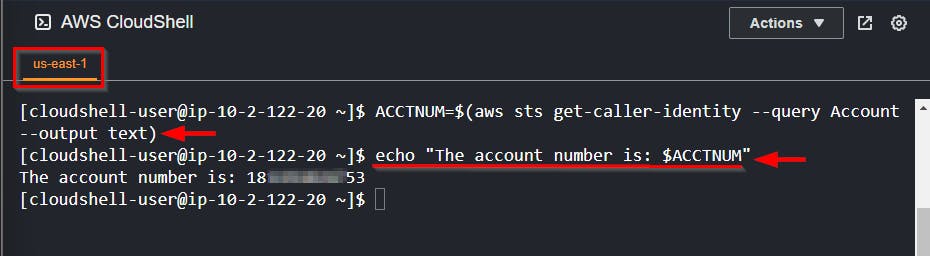
Return to your CloudShell session ( refresh your browser if the connection is timed out)
Run the bash script to get your AWS account ID/ Number
ACCTNUM=$(aws sts get-caller-identity --query Account --output text)
echo "The account number is: $ACCTNUM"
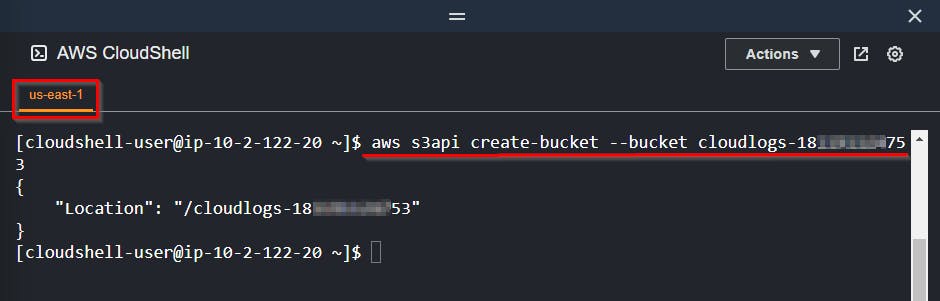
Now, create the S3 bucket with the name of
cloudlogs-followed by your account number.Replace
$ACCTNUMwith your account ID
aws s3api create-bucket --bucket cloudlogs-181191124753
Challenge 3: Enable CloudTrail Trail Capturing Management Events
Navigate to the CloudTrail service's trail section in your AWS console
On your CloudTrail Page, click on the “Create trail” button at the top right
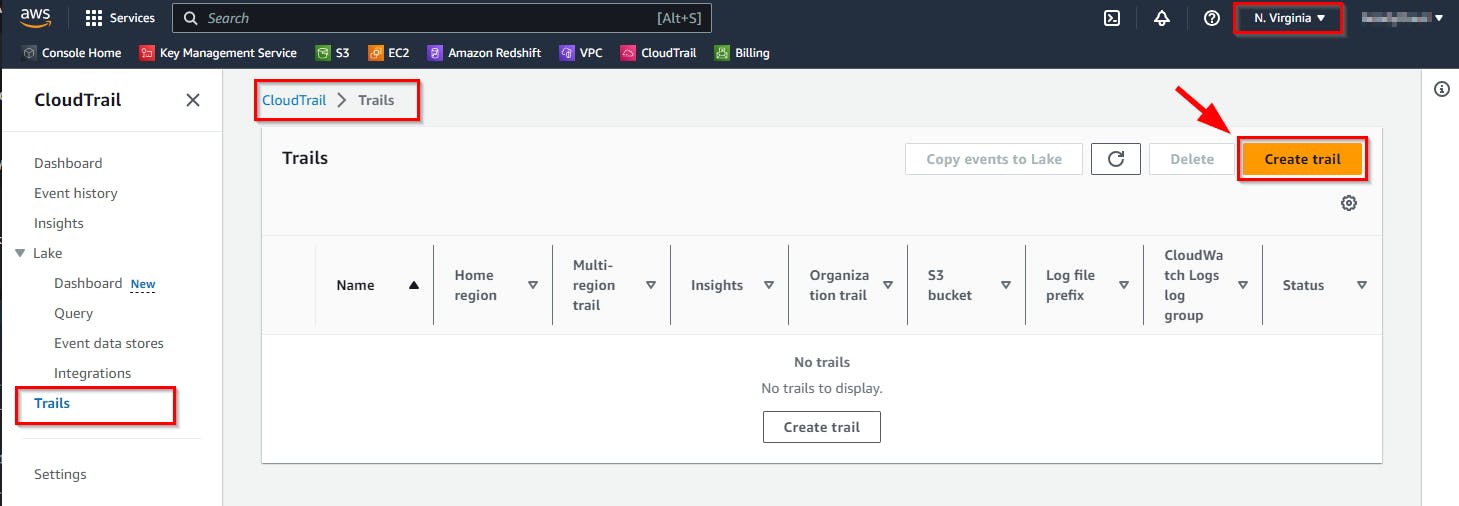
- On the General Details section, give the Trail name "Security,” and under Storage location, select the “Use existing S3 bucket” radio button. Then, click on the Browse button to show the list of available buckets.
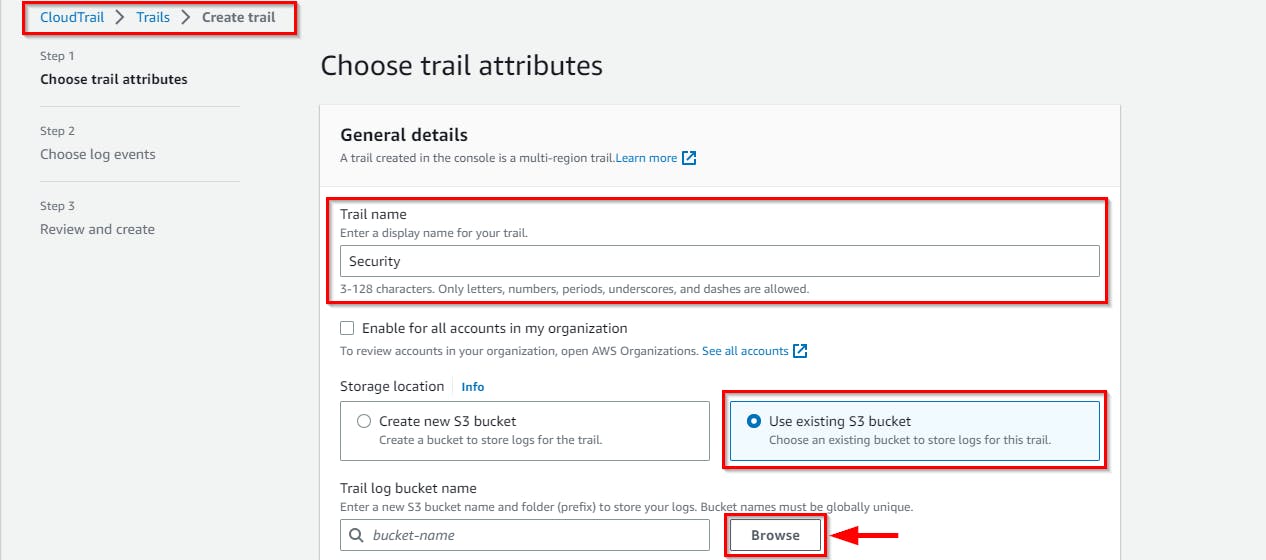
- On the Choose S3 bucket pop-up, select the bucket name
cloudlogs-{your Acct-ID}
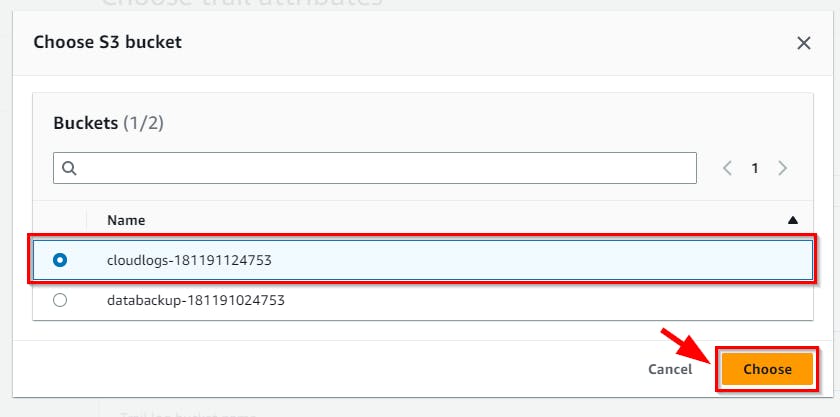
- Scroll down the page and enter the name
security-eventsin the AWS KMS alias text field.
- Scroll to the bottom and click Next
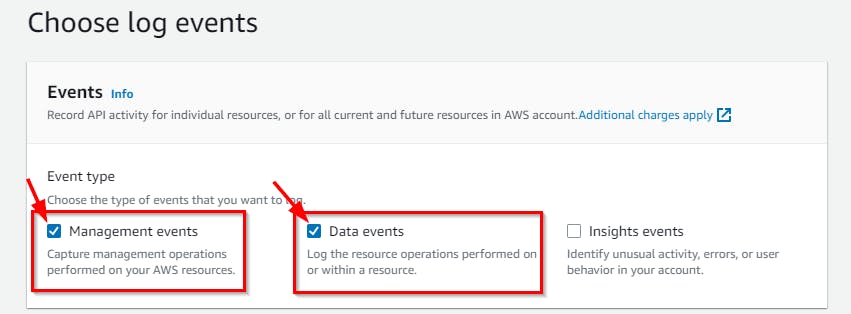
- On the Step 2 page: Choose log events, Under Events, check the box Data events.
NB: By default, management events are selected, but you need to also capture S3 events related to your bucket containing your honey file.
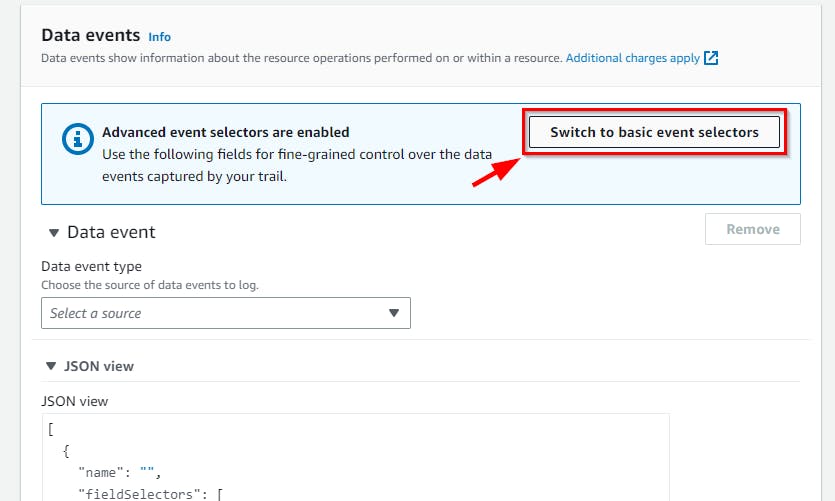
- In the Data Events section, click on the Switch to Basic Event Selectors button. When prompted, select Continue.
- Choose the bucket you want to monitor by unchecking the boxes next to All current and future S3 buckets, then click on Browse.
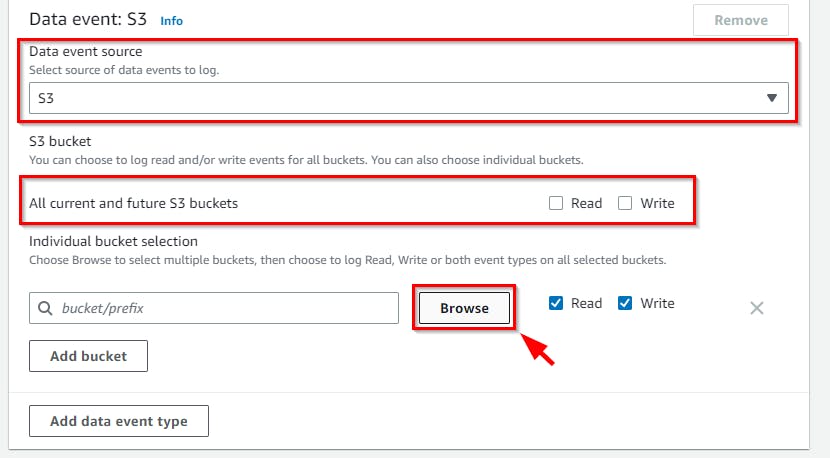
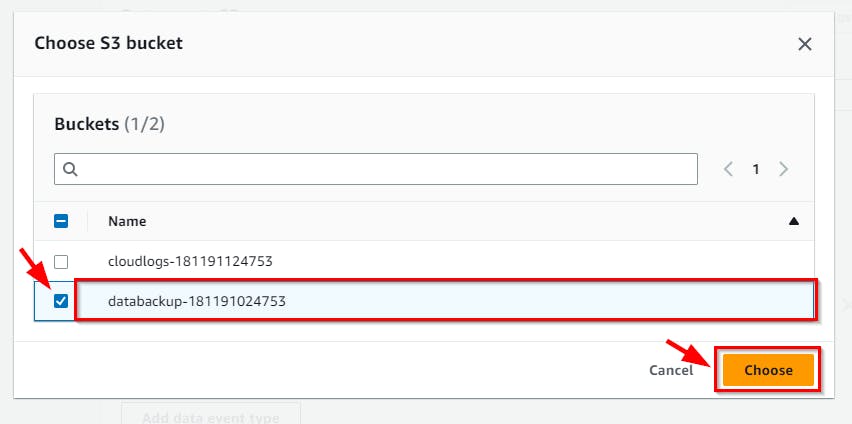
- From the pop-up window, select the S3 bucket to monitor (
databackup-****)and click on the Choose button.
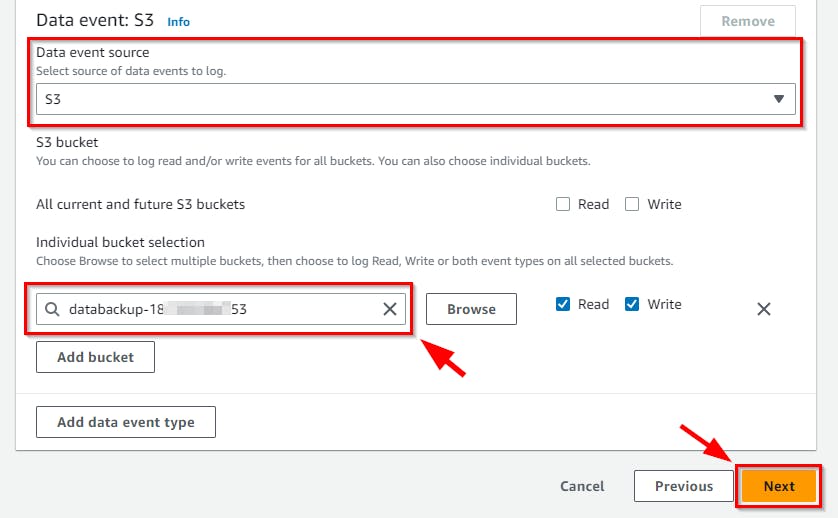
- Scroll to the bottom and click the Next button
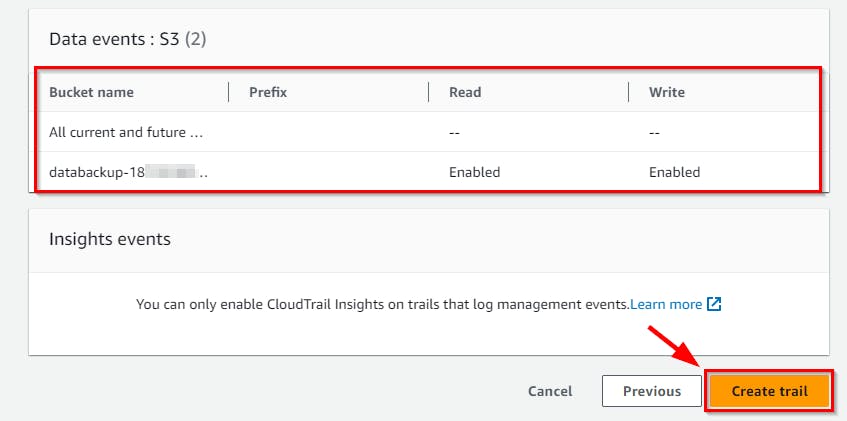
- On step 3, page: Review and create. Evaluate your configuration, and once done, click on the Create Trail button at the bottom of the page.
- CloudTrail has been successfully created
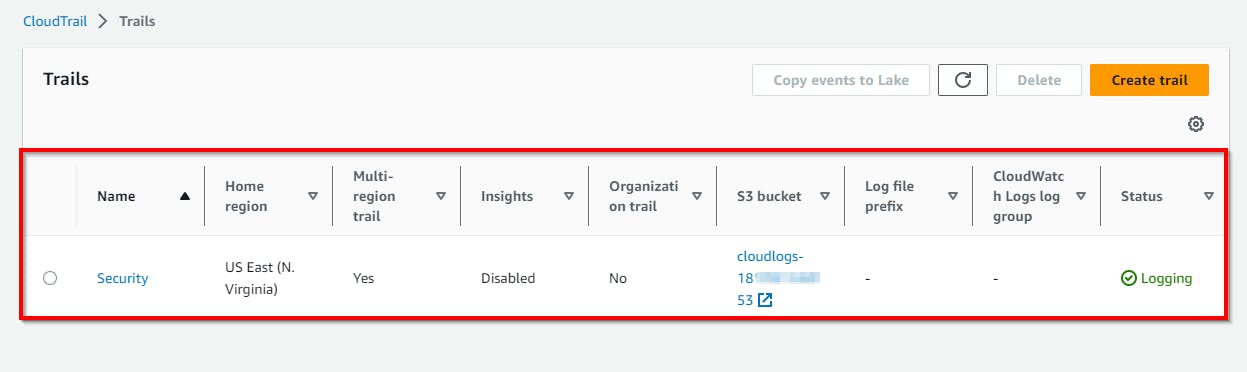
In the current setup, any management activities and specific data events occurring in AWS are recorded and stored in an S3 bucket. In the next lab, you will create event activities by downloading the honey file, which is essential for building the detection process.
